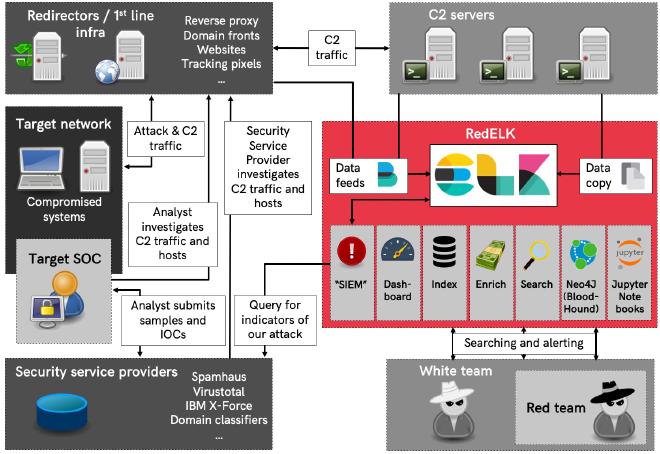
More than 130 Awesome Security Products¹ (In alphabetical order)
¹ Most of them Open Source
Products #
— A — #







— B — #





— C — #










— D — #


— E — #





— F — #





— G — #





— H — #



— I — #


— J — #
— K — #



— L — #


— M — #






— N — #

— O — #






— P — #







— Q — #


— R — #





— S — #













— T — #







— U — #
— V — #



— W — #


— X — #
— Y — #

— Z — #